Key Benefits
- Get full visibility of your attack surface.
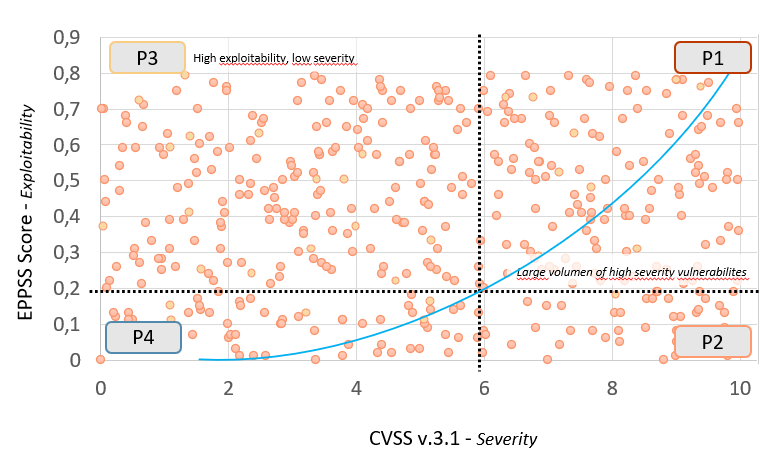
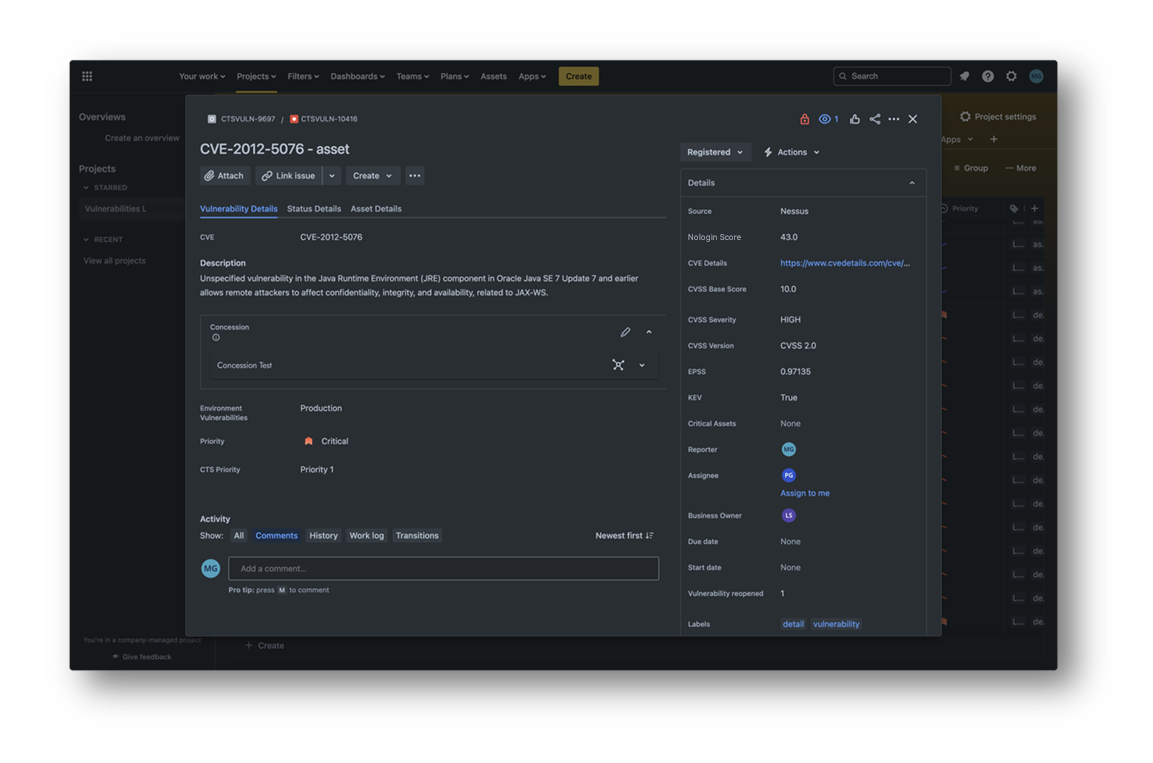
- Communicate the risk of cybersecurity threats accurately through a Nologin Risk Score to all levels of your organization.
- Convert intangible risk automatically into specific tasks, and with a workflow to be resolved.
- Comply with regulations and demonstrate with reports how you are managing cyber risk in your organization.
Prevention cannot be reactive
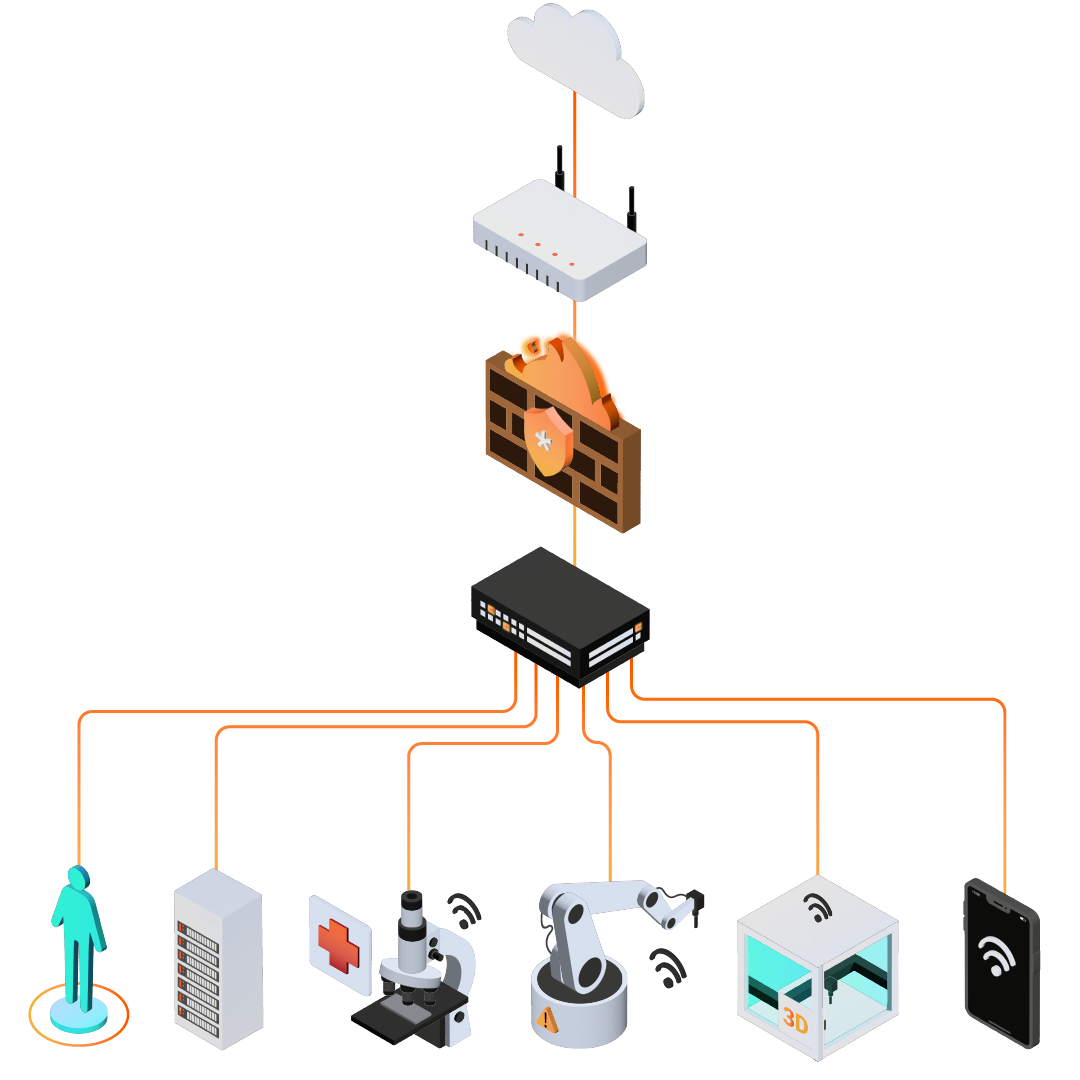
The attack surface is rapidly growing, constantly changing and increasingly interconnected. This poses a monumental challenge for security teams. Whether due to the number of disparate tools for measuring and managing risk, or the volume of items under management, it is more difficult than ever to quantify the impact of risk arising from cybersecurity on business.
Nologin Automated Vulnerabilities Management gives you a unified view of your entire cyber risk exposure, turning that intangible risk into concrete, prioritized tasks, so your team can perform the precise tasks to fix it before vulnerabilities are exploited.